When I first introduced Firepower Device Manager, someone in the audience asked, “Hey! When are you bringing all the features of the central manager (i.e. Firepower Management Center) into the Device Manager?”
I answered, “Never!”
Initially, he was shocked. But when I explained why I said that, he nodded his head.
Firepower Device Manager (FDM) is not supposed to do everything that its counterpart Firepower Management Center (FMC) is required to do. Why?
- FMC is a central manager for managing multiple devices. On the contrary, FDM is supposed to manage only the device on which it’s installed.
- FMC runs on its own hardware infrastructure. On the contrary, FDM has limited infrastructure as it runs on the firewall itself.
- FMC is mostly used by larger security teams, which have different members responsible for different tasks such as access control, security investigations, and device management. On the contrary, FDM is built for a small team (consisting with as few as one) of security generalists.
And, by the way, when did we start believing that Security cannot be simple? It’s a fact that, historically, network security products haven’t always been the simplest to deploy and manage. However, Cisco recognizes that simplicity is a cornerstone of effective security and has taken that to heart as we design our products. The security products should not only protect the organizations but also make the security analyst’s job easier.
That was our motivation when we set out to build FDM, i.e. our firewall device manager.
Because we wanted to make things simple we did a significant amount of research and customer validation every step of the way. We not only questioned every menu item or button that went into the product, but consciously decided to limit the number of things users can do with the device manager. Let me share a couple of examples that illustrate how we brought in innovations to make security simple:
First, we observed that most network administrators spend hours trying to setup the device before trying to configure security on it. We solved that problem by bringing in what we call “easy device setup.” Easy device setup allows network administrators to onboard the firewall using few simple steps. Feel free to look at the video to see how we make this happen.
Second, when you are a small security team you don’t have time to figure out which exact applications, signatures, or file policies you should be applying on your traffic. You expect the security vendors to do that for you and provide options for you to choose. In FDM we did exactly that. We let our best of breed Talos Security Intelligence team figure out risky stuff and provided you options to decide what type of checks you want to apply.
Lastly, in our research, many network administrators told us that, over time, they forget what various access control rules do. It’s hard for them to find out why many rules were configured in the first place. We solved that problem by bringing in an innovative “rule diagram,” which visually depicts what each access rule does. This feature kicks in action as soon as you start building a rule. The picture below shows the snapshot of a rule diagram and it stays there for the entirety of the rule’s life. You can quickly understand what the purpose of a rule is just by looking at it anytime. A picture is worth a thousand words!
Second, when you are a small security team you don’t have time to figure out which exact applications, signatures, or file policies you should be applying on your traffic. You expect the security vendors to do that for you and provide options for you to choose. In FDM we did exactly that. We let our best of breed Talos Security Intelligence team figure out risky stuff and provided you options to decide what type of checks you want to apply.
Lastly, in our research, many network administrators told us that, over time, they forget what various access control rules do. It’s hard for them to find out why many rules were configured in the first place. We solved that problem by bringing in an innovative “rule diagram,” which visually depicts what each access rule does. This feature kicks in action as soon as you start building a rule. The picture below shows the snapshot of a rule diagram and it stays there for the entirety of the rule’s life. You can quickly understand what the purpose of a rule is just by looking at it anytime. A picture is worth a thousand words!
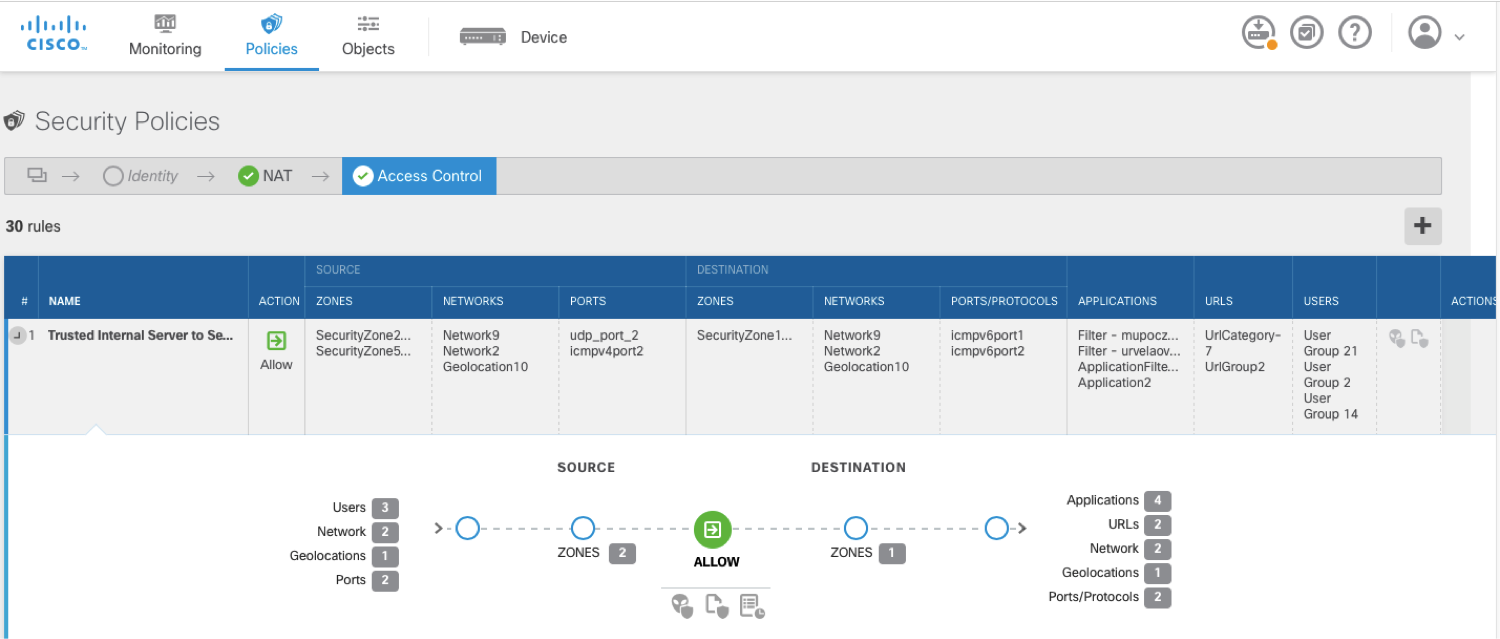
Now you don’t have to worry about why rules were created, even if you inherit a Cisco FTD-based next-gen firewall that was managed by someone else. You will be able to understand rule intent in seconds. Saving you hours, which otherwise would be spent scratching your head. How cool is that?
Having said that, I acknowledge that this is the first release of Firepower Device Manager and we consciously didn’t put every feature in it. But I feel it still packs a punch. While we are busy adding absolutely ‘must have’ features in upcoming releases, we would like to hear from you on what you think.
Take FDM for a spin by requesting a demo through your Cisco representative or partner and let me know whether FDM has made security simple. I would love to hear your thoughts about how we can make it even better.