AI security is getting a lot of attention — and rightly so. Attacks against models, infrastructure and data can cause immediate harm. But security is only one slice of what makes an AI system fit for real-world use. Trustworthy AI is broader: it bundles security with fairness, explainability, robustness, privacy, governance and social impact. Ignoring the “trustworthy” half risks […]
You are browsing archives for
Author: admin
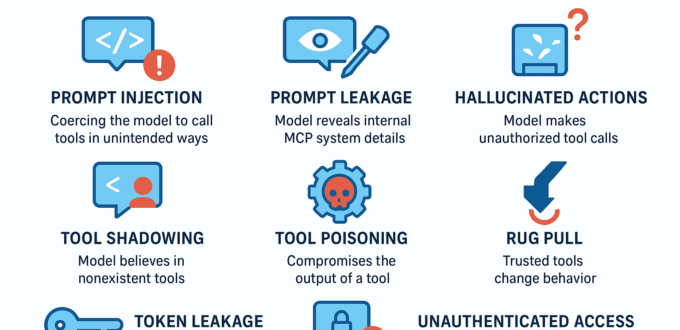
Model Context Protocol (MCP) — Attack La
How to secure agentic systems before they become the new supply-chain problem. As LLM agents move beyond chat windows and gain the ability to execute real-world actions through the Model Context Protocol (MCP), the risk surface expands dramatically. Tools are no longer passive APIs — they’re power. When a model can read files, send emails, deploy […]
Mission: MCPossible – Securing the Brain
On June 16, 2025, Asana notified potentially affected customers–anyone with a user who used the MCP server that an MCP bug was identified. Asana took the server offline and resolved the code issue. They wrote: “Our incident responders and engineering teams acted immediately. As soon as the vulnerability was discovered on June 4, we took […]
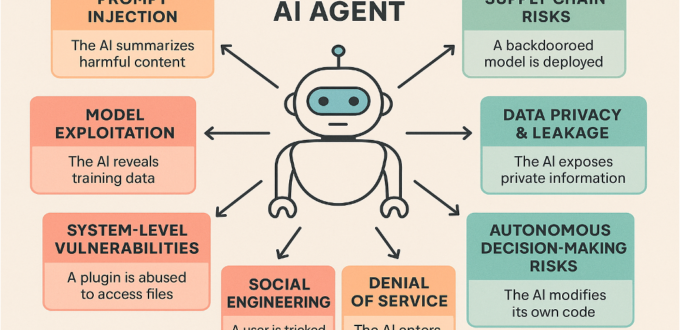
AI Agents Gone Wild: Securing the New Fr...
Recently, I was trying to figure out what we will need to do differently from AI Agent security perspective. Here is what I learned so far but I am sure it’s not enough. Feel free to enlighten me! Welcome to the Age of AI Agents If Large Language Models (LLMs) are like hyperintelligent librarians […]
Of Firewalls and Llamas: What Meta’s Lla
In the world of cybersecurity, we’ve had a long and colorful history of naming things: firewalls that don’t burn, honeypots that don’t stick, and zero trust that ironically requires a lot of trust in the implementation. But this week, Meta added a new entry into our ever-growing lexicon: LlamaFirewall. Yes, you read that right. A […]
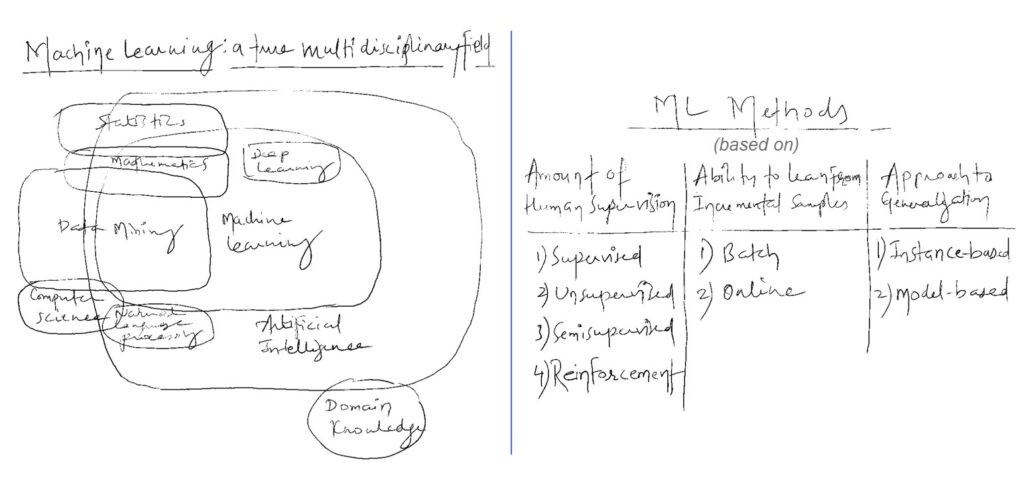
My Take on Artificial Intelligence (AI) ...
Artificial Intelligence (AI) is rapidly advancing and changing how we live, learn, and work. Since I work in cybersecurity, I did some deep dives to formulate my opinion on the topic. In this article, I will explore many ways AI can impact cybersecurity from both the attacker and defender sides. Earlier, I knew we were […]
Review of “Stolen Focus: Why You Can’t P
As a senior technology professional who lived through the earlier half of his life without the internet, I found Johann Hari’s book, “Stolen Focus: Why You Can’t Pay Attention,” to be a real eye-opener. With all the distractions of modern life, it’s no wonder we struggle to focus on anything for more than a few […]
AIBridge Machine Learning Bootcamp for A...
As a technology professional, I’m always on the lookout for ways to improve my skills and stay up-to-date with the latest trends in the industry. So, when I heard about the AIBridge Machine Learning Bootcamp, I jumped at the chance to enroll. I always wanted to learn AI/ML and since this was a free 4-day […]
What did you do differently as a leader ...
The COVID-19 pandemic started approximately a year ago, and shelter in place (also called lockdown in some geographies) began about nine months ago. When it started, I thought it would last a few weeks or at the max month or two. That was an error in my judgment. Soon it dawned upon me that it […]
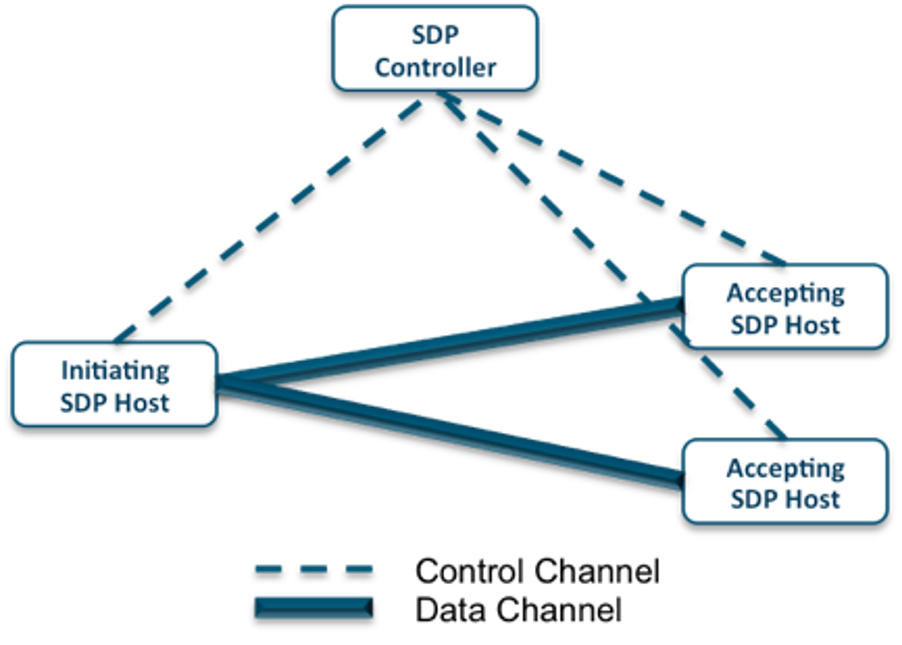
Cybersecurity Alphabet Soup: SDP, ZTNA, ...
The technology industry is a breeding ground for creating TLAs (Three Letter Acronyms) and FLAs (Four Letter Acronyms). So, having a few more TLAs and FLAs to the party is just normal business. In recent years, SDP and ZTNA have caught up, and in the year 2020 a new term SASE has picked up the […]