The technology industry is a breeding ground for creating TLAs (Three Letter Acronyms) and FLAs (Four Letter Acronyms). So, having a few more TLAs and FLAs to the party is just normal business.
In recent years, SDP and ZTNA have caught up, and in the year 2020 a new term SASE has picked up the momentum.
If you don’t know what all these terms mean here are quick definitions:
Software-Defined Perimeter (SDP)
Software-Defined Perimeter (SDP), also called a “Black Cloud”, is an approach to computer security that evolved from the work done at the Defense Information Systems Agency (DISA) under the Global Information Grid (GIG) Black Core Network initiative around 2007.
Source: https://en.wikipedia.org/wiki/Software_Defined_Perimeter
If you don’t want the technical jargon, then think of SDP as an architecture that separates the control plane from the data plane while connecting users to the network. This separation helps to achieve access control, asset isolation, high availability, and scale.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) is another security architecture where the only traffic from authenticated users, devices, and applications is granted access to other users, devices, and applications.
Source: https://www.sdxcentral.com/security/definitions/what-is-zero-trust-network-access-ztna/
Does that read similar to SDP to you?
If yes, it’s because they are similar. But since different organizations initiated these terms, they have different terminologies. There are some subtle differences as well.
For example, when John Kindervag from Forrester first talked about Zero Trust in the year 2010, he talked about Zero Trust Network Architecture. The zero-trust principle i.e., “never trust, always verify” was envisioned to address the broken traditional trust model.
Today’s ZTNA i.e., Zero Trust Network Access is a way to achieve Zero Trust for the access part. You would still need to inspect the traffic for you to achieve complete Zero Trust.
SDP, on the other hand, provides much more prescriptive architecture (see the picture below) that separates the control plane and the data plane.
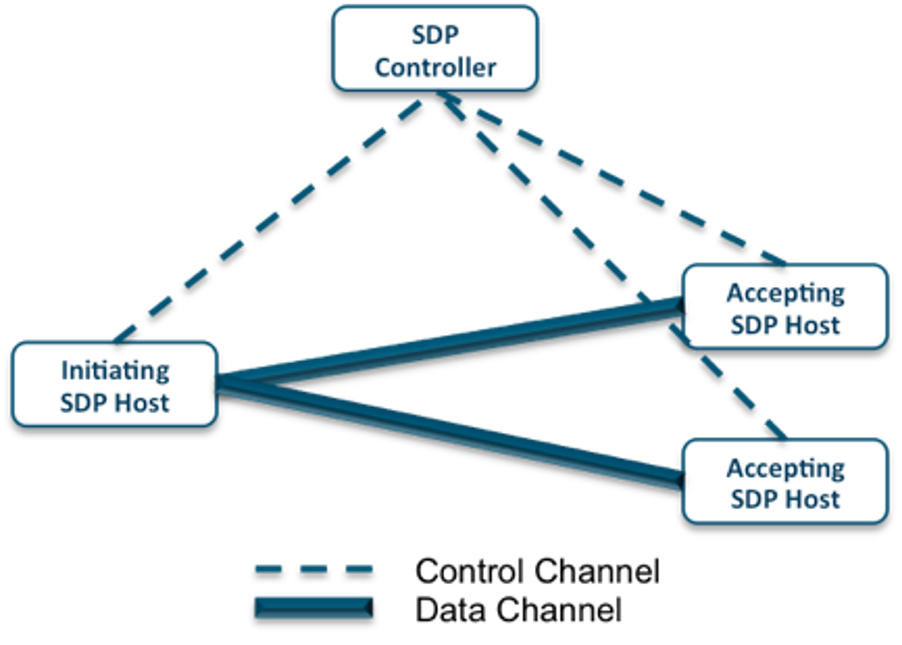 Source: Cloud Security Alliance
Source: Cloud Security Alliance
Once you do that it’s easier to control access to the network based on various parameters such as user, device, time of the day, location, etc. The SDP architecture also mandates granting least-privileged access defined by the granular policies.
So, if you think about ZTNA carefully you will realize that it actually uses the concept of SDP.
Secure Access Service Edge (SASE)
This is a recent term that Gartner introduced in August 2019 when they released the “Future of the Network Security is in the Cloud” research report.
Source: https://www.gartner.com/document/3956841
As per Gartner analysts, SASE combines network security functions (such as SWG, CASB, FWaaS, and ZTNA), with WAN capabilities (i.e., SD-WAN) to support the dynamic security needs of the organizations.
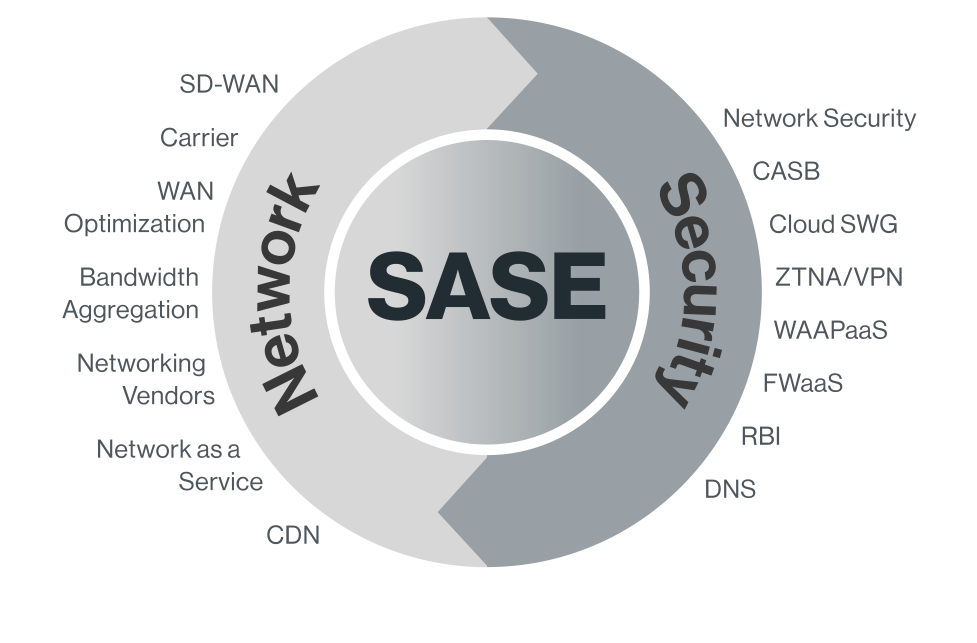
Source: The Future of the Network Security Is in the Cloud
These capabilities are delivered primarily as a service (aaS) and based upon the identity of the entity, real-time context, and security/compliance policies.
Does that term SASE feel like an umbrella term then?
If yes, that’s because IMO it is.
Today, the biggest challenge for all the cybersecurity vendors (SonicWall included) is to justify that they have SDP, ZTNA, and SASE solutions so that their customers don’t feel like they are missing out on the innovative trends.
So, we have the following types of vendors, which originated in different cybersecurity domains trying to pitch their solutions as SDP, ZTNA, and SASE.
- Cloud-delivered cybersecurity vendors – Recent additions to the ecosystem
- IdP vendors – Identity Providers
- SD-WAN vendors – Software-defined networking players
- New vendors – New companies that get added to the ecosystem (as purists) with every new wave of acronyms
- Traditional cybersecurity vendors – Birthright, indisputable, right?
Who will win the race?
Time will tell! We just have to wait for a decade or two!